The Cyber Essentials scheme was set up by the government and a group of cyber security experts to help many small to medium sized companies become digitally secure against 80% of known cyber threats. In this blog we will explore how Cyber Essentials could help your business, point you to several ways of implementing it, and suggest other things you can do to make your network secure.
-
BONGO IT BLOG
BongoIT News
Microsoft has released Windows Server 2016, but what's new? What's been improved? And what hasn't? Hopefully this overview will give you an idea of if it's worth the upgrade or not.
SIP Trunking: VoIP's Perfect Partner
Voice over IP (VoIP) telephony has been gaining traction for some years now, but many businesses have yet to take advantage of SIP trunking, a technology essential for the full realisation of the benefits of VoIP and other tools.
SIP (Session Initiation Protocol) is a communications protocol designed specifically for multimedia communications running over Internet Protocol (IP) networks, such as the typical company network, and the Internet itself. It is most commonly used to underpin VoIP, video call and instant messaging applications.
With the end of the final TV debate of the 2016 US election, what is left that could change the results of the November vote? Analysts claim that Facebook’s "I Voted" button could have a potential influence over voter turnout. The so-called "Voter Megaphone" allows you to show that you have voted and see if your friends on Facebook have also voted. But by how much could it change the Presidential race in the US and its polls?
A recent study finds that one quarter of law enforcement websites based in the UK have a weak connection and could be prone to hacker interception.
Millions of people have recently found out that they not only have a Yahoo account but also that it has been hacked. Many large companies such as BT use Yahoo to base e-mail accounts for their customers. Anyone with an email address ending with "@btinternet.com", "@btopenworld.com" or "@talk21.com" could have been indirectly hacked and their details leaked.
"Without the superb help I recieved from Justin and Andrew at Bongoit, I would not have been able to regain ownership of my businesses online presence."
"6 months ago a contractor who worked at my family business attempted to steal it from me. By the time we caught him out and involved the police he had stolen our domain name, goode review account authority, controlled a website in my business name and was passing himself off online as the business owner. This had a devastating effect on my customer retention and the ability for prospective customers to even find my phone mumber.
Without the superb help I recieved from Justin and Andrew at Bongoit, I would not have been able to regain ownership of my businesses online presence. At every stage they were key in providing the help and support I needed. No matter how busy they were, what time of day or how little notice they recieved, they were there, on the phone and ready to talk my solicitors through aburdly complicated internet/legal jargon and provide expert testimony that without doubt was the deciding factor ond turned the tide.
5 stars is not enough.
Use BongoIT if you need help.
Thank you Bongo!"
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
In recent reports it has been found that the Chinese tech company Lenovo has made their most recent batch of laptops locked into Windows 10. Many have suspected that they had a deal with Microsoft but Lenovo has denied this. This, however, is not the first time Lenovo has tried to constrict what user are able to do on their hardware.
The Supposed Deal With Microsoft.
A Lenovo spokesperson claimed the Chinese giant "does not intentionally block customers using other operating systems on its devices and is fully committed to providing Linux certifications and installation guidance on a wide range of products". The accusation originated from a Reddit thread. The thread accused Lenovo and Microsoft of locking the operating system onto the laptops at a firmware level. Lenovo stated that the lock was a storage driver compatability failure and not a feature."Unsupported models will rely on Linux operating system vendors releasing new kernel and drivers to support features such as RAID on SSD," the spokesperson staited. This meant that if you want to install Linux, you need a kernel with the required SSD driver. The issue could be simply that the latest kernel for Linux RAID has a small bug that creates a huge problem. The affected models include the "Yoga 900S" and the "Ideapad 710S". This does not bode well for Lenovo's already shaky record of unnecessary firmware additions.
BIOS Editing
In August Lenovo sold laptops with that came with free crapware already installed. This included free demos, unnecessary Microsoft programs and other things that clog up your storage space. The software itself was attached to a BIOS function which detected if any of the crapware is deleted and then reinstalls them for you on the next boot up of your system. The way that Lenovo had created their BIOS for the laptop range was with a WPBT that allowed manufaturers to add their own programs and drivers to your operating system.It was also designed to help prevent corruption by running executables on boot-up. This, however, gives companies like Microsoft a free backdoor to implant free, unremovable, demos and software. This idea of implanting information into the operating system was supposed to be used by anti-virus programs. The idea being that that protection programs could delete viruses that had placed code into the BIOS of your system. But the advertisement of major companies beat any hackers that could figure the vunerability out. But that's not all, Lenovo also sends a moderate chunk of statistics back to their databases in China.
Will Lenovo clean up their act? Or will they continue their scheming ways with Microsoft? We can only wait and see if history repeats itself once more with Lenovo.
Lenovo crams unremovable crapware into Windows laptops – by hiding it in the BIOS
Lenovo denies claims it plotted with Microsoft to block Linux installs
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Follow us here LinkedIn or here Twitter
This handy piece of software allows you to block almost all ransomware - including the dreaded cryptolocker.
Ransomware Prevention, now for Free.
This invaluable piece of software, now given to the public for free, can clean up and prevent most malicious attacks that come in the form of ransomware. The "Cryptolocker Prevention Kit" was only given out to paying subscribers but now it's available to all. It is not something that can replace your anti-virus but it is a usefull addition to your PC's defences. The kit boasts an "article on cleaning up after infection but more importantly materials and instruction for deploying preventative block using software restriction policies". This means that if your computer gets infected by something that is trying to modify existing software it will be blocked from your machine and placed into quarantine.
The SMBKitchen Crew and Third Tier staff had origionally made this program only available to paying customers. But due to the rapid spread of the virus, the producers made it available to everyone. Click here for the download page.
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
In the aftermath of Cryptolocker and Gameover Zeus, is the threat of ransomware still significant? How does ransomware work? How can ransomware be prevented or even removed form the internet completely?
The fight against ransomware and all viruses in general is always an uphill struggle. Your typical anti-virus programs can only prevent attacks from viruses and malware from programs it recognises as threats such as the famous Crytolocker.
In June last year the network provider and multi-million dollar company Ubiquiti was scammed out of $46.7 million and has since been only able to recover $8.1 million with prospects of another potentual $6.8 million. This one blunder will set them back at least $31.8 million. These crimes have inspried other CEOs and executives to fight back against the criminal hackers.
Florian Lukavsky Uses Hackers Own Techniques To Stop Them.
SEC Consult Singapore director Florian Lukavsky has turned predator into prey by creating a hack that sends scammer's Window's 10 credentials to the local police. Scammers like the ones that caught out Ubiquiti use a technique of e-mail spoofing to convince executives to wire large amounts of money into their own accounts. The victim doesn't usually find out that they have been scammed untill several hours later. Banks usually don't refund this type of fraud and it is usually written off as a buissness blunder. Florian Lukavsky's counter-hacking relies on the fraudsters making a blunder that could not only cost them their ill gotten gains but also jail time. After a executive has been scammed Florian Lukavsky sends an e-mail to the attacker which seems like it is a transaction comformation from the victims bank. This e-mail includes a pdf file which contains a virus that when the attacker (hopefully) opens will find as many credentials as it can from their linked Outlook or social media accounts account and then immediatly wires it to the police.
"Someone impersonated the CEO of an international company requesting urgent wire transfers and a couple of hours later they realise it was a scam … we worked together with law enforcement to trick the fraudsters," Lukavsky says. "We sent them a prepared PDF document pretending to be transaction confirmation and they opened it which led to Twitter handles, usernames, and identity information." Lukavsky says that he gets a "kick" out of convincing scammers to fall for their own trick. His efforts have led to many arrests and shut downs of many scammers and their bank accounts based in Africa.
Where does the Lost Money Go?
Ubiquiti, which lost $46.7m in June last year isn't alone in the losses. Belgian bank Crelan, which lost $78m in January, Accenture, Chanel, Hugo Boss, HSBC, and countless other smaller companies have also fallen victim to e-mail spoofing and phishing attacks. The FBI estimates some $2.2billion has been stolen from nearly 14,000 cases in seven months to May this year Some $800m in losses occurred in the 10 months to August 2015. Obviously the money can't go through the conventional route it was intended for, so where does it go? Most scammers that are impersonating another person send the money to a bank in China's Wenzhou region. The region itself has been known for money laundering for many international crimes and scams. After the money leaves that bank, any attempt at tracing it's path is practically impossible. After it leaves a chain of Chinese banks it would likely end up in the personal bank accounts of scammers like the ones Florian Lukavsky stopped in Africa.
Donald McCarthy Prefers Prevention Over Counter-Attack
Vice President of Operations at myNetWatchman LLC Donald McCarthy has an alternate way of preventing his workers form falling for phishing scams. He belives that anti-phishing is more of a deterrent than counter hacking like Florian Lukavsky. Donald McCarthy has come up with a program that will allow his workers to recognise and report phishing e-mails. His idea includes sending out "mock" phishing mail to members of his workforce and reward them for reporting it or making sure they know what could have happened when they believe them. Over time, as the workers get a better sence of what is and isn't a phishing scam, McCarthy will increase the difficulty by making the e-mails that are pretending to be phishing scams less and less obvious. He says that he often rewards employees for the successful identification of a scam with gift cards and in-office snacks.
"I think all organisations greater than one person should use anti-phishing," McCarthy says. "Even that one person should use it".
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Follow us here LinkedIn or here Twitter
Source Articles:
Anti-phishing most critical defence against rife CEO email fraud
The new cloud regions in the UK become part of one the world’s largest online storage infrastructures, supported by more than 100 data centres globally. Several large organisations have already signed a new contract with Microsoft to use these new data centres including the Ministry of Defence.
Microsoft has recently opened several data centers in the UK. For the First time ever UK users of Azure and office 365 will be able to connect to their data without it having to pass through another country to get here. This new investment makes Microsoft the first global service to provide data from a cloud based from UK data centers. Many large organisations such as Glasgow City Council, Marks & Spencer, Confused.com, Natural Resources Wales, Pizza Hut Restaurants and Virgin Atlantic already use Microsoft's cloud servises and the Ministry of Defence is soon to join them.
Better Security and Speed For the Ministry of Defence.
The Ministry of Defence has stated that it has signed a contract to make use of the new UK based data servers because of both value for money and security of data. The MoD not only has around 230,000 workers, many of which will use Microsoft cloud products like Azure but also spends around £3 billion each year to improve its data infastructure. This should give you an idea on how much Microsoft has invested into the capacity and security of these servers.
“Microsoft’s secure and transparent cloud service in the UK fits perfectly with the MoD’s digital transformation agenda,” said Mike Stone, Chief Digital and Information Officer at the MoD. “This agreement, which is based on Microsoft’s world-class reliability and performance, will allow us to deliver cost-effective, modern and flexible information capabilities. It will ensure we are better-placed in our ever-changing, digital-first world”. Mike Stone also stated in a BBC interview that this is a welcome change as many elements of the MoD's servers and software hasn't been updated for several years.
The New Investment is a Welcome Change.
"We were still on Windows XP, for instance, and all of the applications were from 2003 or prior to that," he said in a recent interview. "I took the view that the services we were providing were unfit for purpose. The idea is to provide a different capability that fully exploits the power of the cloud and mobility. We can now work on documents collaboratively and understand more about the ways we are working—we will be able to see how much time teams are spending in meetings, on email and on the phone.".
Before Microsoft had installed these local data centers our data was having to pass through several countries. The Neatherlands and Ireland had the largest amount of traffic within their Microsoft data centers due to it having to pass through them to get to UK users. Now UK users will be able to enjoy the global network of Microsoft products such as Azure and Office 365 with less latency and more capacity but with the bonus of added security due to local servers.
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Follow us here LinkedIn or here Twitter
Source Articles:
MoD inks UK Azure data centre deal with Microsoft
Microsoft becomes first global provider to deliver complete cloud from UK data centres
Is The U.S. Bluffing About Their Cyber Security?
At the G20 summit in China yesterday, President Obama stated that: “We have had problems with cyber intrusions from Russia in the past, from other countries in the past.” and that now “we are moving into a new area where a number of countries have significant capacities. And frankly we have more capacity than any other country, both offensively and defensively.”.
Are Americans at Risk?
This would obviously be reassuring for any nervous American not wanting to be spied on by countries rival to the United States but a quick read of a report made on the 5th of August may make them worry once again. In a presentation at a "DEF CON" hacking conference Jason Healey, a senior researcher scholar at the University of Columbia, revealed his report on the number of zero-day vunerabilities that U.S security agencies have at their disposal. Healey expected that the U.S. would have useable bugs in the tens of thousands. After his research into released documents, Snowden leaks, interviews with intelligence staff, and presidential papers he concluded that there could not be more than fifty bugs in total. He was sure to state that the true number of bugs and stored vunerabilities that the U.S. intelligence has could still be a mystery but the evidence found to support a severe lack of cyber strength is compelling.
So does this mean Obama was bluffing at the G20 summit, perhaps in some way to disuade potentual international threats? Or has the U.S. been able to amass a massive proportion of new bugs and vunerabilities within a month?
What are "Zero-Day Vunerabilities" and Why Doesn't America Have Them?
Zero-Day vunerabilities are bugs or vunerabilites in systems that could allow organisations like the NSA or CIA to counter-attack in the event of a cyber war breaking out. However the bugs themselves pose a threat. For as long as the United States government keeps them there is the chance of a leak and hackers obtaining these secret system vunerabilities. This has divided American politics on the subject, as many would like to keep the bugs in case of a threat from China or Russia would arise, whereas others think more businesses would invest in the United States if they knew the threat of hackers obtaining these bugs were low or non-existant. So due to this division in opinion we end up with something like the results from Jason Healey's report staiting that the U.S. is not a major power in cyber world and also President Obama telling the U.S.'s main rivals that they will be the best on the cyber battlefields to come.
All the evidence suggests that the U.S. did not meet the same cyber power as expectations but could be working towards fufilling them in the near future after the G20 summit.
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Follow us here LinkedIn or here Twitter
Source Article:
Identity Theft Is On The Rise
Readers be advised, idetity theft is on the rise. In the UK alone there were 148,000 victims during 2015 according to the fraud prevention service Cifas. This is up by 57% from previous years. And as if we were not worried enough by Ransomware and Brexit!
Researchers looking at this growing issue have identified social media sites as the main culprits for publishing personal details. If you think about it you wouldnt give your date of birth to just anyone, but there it is on your Facebook wall.
These personal details can be used to take out things such as loans and credit cards in your name, and could land you with a whole heap of debts, The advice is to be aware, and think carefully before you put any details online, and keep up to date with security/privacy settings for the sites where you have posted your details.
It could be something else that gives the game away for enterprising fraudsters though such as a photo that has your bank card it in somewhere, a picture with your passport in (perhaps if you are going on holiday), your phone number (Yes even that can be used as fraudsters may try to run a scam on you!).
So remain vigilent and don't let the fraudsters catch you out...On the other hand I don't get a huge stream of Happy Birthdays on my Facebook wall, sad days indeed.
Ability To Control Shared Mailboxes Sent Items In Office 365
What is it?
The ability so keep a record of emails being sent and who sent them when using a shared mailbox. This feature is especially useful when using a shared mailbox which could have several users, and is essential for some businesses.
In Exchange 2010 there was a way to configure how sent items were set up for shared mailboxes, but this was left out of Exchange 2013. Since reviewing the customer needs (i.e. customers screaming at them for removing the feature) Microsoft have re-released this handy feature.
How does it work?
Emails can now be sent as the shared mailbox itself for example from This email address is being protected from spambots. You need JavaScript enabled to view it., or by the individual users. Either way will now retain a copy of that message including the sender details in the sent items for that mailbox.
Do I need to do anything?
Yes, as by default this feature is disabled. It can be turned on by setting the features' enable flag to True. You will likely need IT Support to help you with this but for more information please see this Microsoft article Technet
Enjoy the blog post? Then you would love our newsletter! Signup here and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Have you just upgraded to the latest version of Office 365 and found that the way attachments work has completely changed?
Office 365 now sends links to documents instead of the file itself to save space.
Some of our clients have been calling in about this issue/change for a bit of IT Support. Microsoft will implement new features without making end users aware. This feature has been on the development roadmap for a while though and is designed to save storage space in Exchange online, and improve workflow. It also probably saves Microsoft a bit of electricity in their data centres, probably.
Where do I see this feature?
When you open a new email in Outlook 2016 and you want to attach a file most users will click the attach button in the email menu. Doing this now will present you with a list of the most recent documents you have used, and should the thing you are looking for not be there the option to browse for the file.
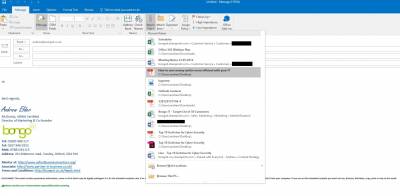
Once you select a file it will seemingly attach itself to the email.
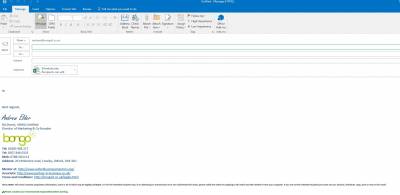
The good news is that you can still easily attach documents. All you need do is click on the dropdown menu for the attachment and choose "Attach As Copy".
Why use the link sending feature at all?
Internally to your business it makes a lot of sense. Documents should be worked on through the system so they are always saved, and if versioning is turned on then versioned as well. We all spend a lot of time looking for things in our filing systems too, this should help users get to documents quicker, and ensure everyone is working on the same document version. Externally however it doesnt really work as a concept, yet.
Enjoy the blog post? Then you would love our newsletter! Signup here and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Follow us here LinkedIn or here Twitter
Saving Money and Increasing Efficiency in IT
With the uncertainty generated by BREXIT, the economy generally being a bit slow to pickup during the first half of 2016, and with the price of oil seeming to creep back up, the future seems uncertain and everyone is looking at how to save a bit of money. The question is can you save money and be more efficient at the same time?
The short answer is yes but you have to be willing to change, and those changes in the short term will cost money and/or time which is recouped in the medium to long term. Trying to be frugal on the following solutions and do it yourself can, unless very well managed, cost you a great deal more time. After all, you get what you pay for.
An example of change and efficiency working hand in hand to increase revenue: A UK technology provider is forging their own path to growth by diversifying their business and using their hard won efficiencies to nurture a new business arm. Fidelity-Group have traditionally been in the leased line and telecoms market but are now heavily promoting their energy savings arm. Their rationale is that the systems and processes needed to manage quoting and billing are very similar. In this way they are using their strengths to build a new market for far less upfront cost than say a new company would experience.
As we are from the IT world though we wanted to give you our top ten tips on saving money on IT whilst increasing efficiency, and none of them involve firing anyone.
- Get rid of your server and its maintenance. Whilst this isn’t suited to a company doing in house software development there are still thousands of small companies out there running Microsoft Small Business Server for nothing but email, calendars, contacts and file sharing/backup. Often the way these have been setup is haphazard and leaves gaping security loopholes but that is another story. The point is if this sounds like you then you need to consider moving to Office 365. Let Microsoft look after ‘your’ server in their massive, purpose built server farms. Let them deal with updates and maintenance. Not only is it virtually guaranteed to save you money and time but with a correct implementation and the appropriate training you can become more efficient too.
- Get a better hardware supplier. Do you ever find yourself walking in to PC World to pick up a new computer? Oh dear, not only are they expensive but the tendency is to, with the best intentions, buy something with all the bells and whistles that you just don’t need. The same goes for many small computer supply shops. The problem is being able to trust that what you will get is fit for purpose without trying it first. To be honest though, should you be making that decision? Your IT guys should know what applications you need and buy the PC that is fit for purpose. Get a standard workstation from an industry supplier, and have it delivered to site the next day. No need to think about it, no need to drive/walk anywhere.
- For that matter get a better software supplier. Some hardware suppliers will also do software so long as it relates to the systems they sell. For example a large distributor of Dell will probably also do Kaspersky licenses for a fraction of the price you would pay from the Kaspersky site.
- A minor point, but something you can implement right away. Did you know that ~85 per cent of UK landline phone numbers are registered with the Telephone Preference Service, but only 3 per cent of mobiles are signed up to the service (which is mostly free)? Whilst this won’t save you money directly it will save you time from answering those pesky sales calls. Just text “TPS” to 78070.
- Hire an accounting expert, perhaps just as an advisor or on a temporary contract. They should be able to help you make cuts which don’t just get shifted on to another business unit. You may also be able to tap legal resources to review existing supplier contracts.
- Take control of “unmanaged” costs such as power consumption, or printing. Ensure you can measure these costs accurately so you can see where you can make further savings.
- Get rid of useless software. We all have that subscription somewhere that eats away at our bank account until we notice one day and wonder why we ever bought it in the first place, or in some cases IF we even bought it! It could be the anti-virus software you used to use, or even the current software which can often be bought cheaper through a different supplier. Is it strictly necessary? Does anyone use it? Isnt there an open source version you could use?
- Switch to VoIP telephony. Typical savings are in the 40% region. You will need a good internet connection to do this but even the Virgin home broadband upwards of 100mbps is good enough for a dozen people (though not if you run a call centre).
- An obvious one – review your marketing plans often. Are you getting a return on any of your expenditure? Are you spending enough in the right places or just throwing money at a marketing spread where its impossible to tell what is working and what isn’t? For example if sending a branded Filofax to a highly targeted prospect costs £200 but they become a high value customer for life is that not better than sending 10,000 emails to fairly random people?
- Rationalise your systems. Emails, websites and failover services are high on the list for this. If youre a bit worried about touching it (using the “if it isn’t broken” rule!) get in a consultant to help make it more efficient moving forwards. So much can be done on the cloud today, and often it presents a much more economical option.
Conclusion
You are not expected to know everything. Equally though when was the last time your IT company came to you and said “hey, we have this great idea that will improve your business/an aspect of your business, and it is really easy to implement”? And then it happened, it was easy/cost effective, and it made a difference?
Do we practise what we preach? To some extent yes we do, we invest back in ourselves in new learning, certifications, and IT equipment and software to do our jobs better. We have embraced the cloud and learned to use the tools it gives us to be more efficient. We have also just refurbished our office which now looks respectable enough to not be embarrassed about bringing clients to. So why not come and visit us for a coffee if you are ever in Oxfordshire?
Enjoy the blog post? Then you would love our newsletter! Signup here and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
The internet has revolutionised how many businesses operate, and how we live our lives. With over 2 billion users it is also a battleground for cyber security experts and hackers. Protecting key information is often critical to the survivability and competitiveness of businesses today.
Cyber security is also a hot topic at the moment with the government pitching in with adverts to warn us about using stronger passwords; but there are also some very common mistakes we see IT technicians making all the time. Here’s our list of the top 10 security gotchas.....
1. Port forward 3389.
Are you able to remotely login to your server using this method? Restricting access at the Firewall by IP address is not good enough as IP addresses can be spoofed and your details could be “sniffed”. This is called a man in the middle attack. This is such a common issue seen all the time, poor practise creates loopholes!
2. Sharing passwords across clients.
The chances are that the companies which do this will also proudly list some of their clients on their website. Therefore an enterprising person could gain access to all or some of said companies’ clients. The worst culprits seem to be website "designers"
3. Installing 3rd party browsers (like Chrome or Firefox) on to a server, and/or disabling Internet Explorers’ protected mode.
Why would an admin do this? Because it’s difficult to browse from a server otherwise. IT technicians should instead connect to a workstation, browse from there and if needed download files to a shared folder.
4. Poor physical security.
If I can touch your server I can take everything you have. This is quite a remote possibility for most people, but for businesses in highly competitive markets and with valuable Intellectual Property it can be an all too easy mistake to make. For example we have noted that it is usually very easy to get in to a “secure” premises by saying “I’m here to fix the computers”, people tend to just trust you!
5. Creating/not noticing SQL injection vulnerabilities.
These are unfortunately all too common given that they can be easily avoided. One of the most notable cases was the SQL Slammer worm of 2003 which infected ~75,000 machines successfully within 10 minutes of deployment. An amusing yet simple example of SQL injection is the tale of Little Bobby Tables. His mother being the caring sort we all know and love decided to Christen her son “Robert’); DROP TABLE Students;” which when typed in to the school database (as part of standard data entry probably done by an unwitting intern) erased a years’ worth of student data. Obviously they should have sanitised their database inputs! XKCD.
Primary Defences:
- Use of Prepared Statements (Parameterized Queries)
- Use of Stored Procedures
- Escaping all User Supplied Input – Probably the best method!
6. SSL Issues
SSL certificate expiry happens to the best of us, well not us, but some very big companies like Google in the case of their Gmail service. It can be very embarrassing when clients can’t access your website/their email, and potentially damaging to your reputation when they are told it is not a trusted domain. To ensure it doesn’t happen make sure you get the email reminders from your certificate issuer, and that these go to a shared inbox where designated people can action it.
7. Automated Patches
Windows Server Update Services (WSUS). If not configured properly the WSUS will use Http not the encrypted HTTPS delivery. Hackers could use low-privileged access rights to set up fake updates. These updates could download a Trojan or other kind of Malware allowing the hacker some access to your server.
8. Sensitive data exposure
A good developer should be very aware of security, sadly many developers are not. We had a situation like this when we took on a charity who had a lot of work done for them pro bono. We always say that you get what you pay for, and in this case that really rang true. The (very) sensitive data was not encrypted, nor was the access to the data. Anyone working at the web hosting company had access to the data, we had access to the data, the data could have been sniffed etc. and whilst we can be trusted we shouldn’t have access, and Joe Blogs is definitely a security threat.
9. Not applying fixes/updates
In a lot of SME’s they tend to look after their own IT until it becomes too complicated (out of necessity) for them to manage. I can’t count the amount of times I have gone in to scope out a system and found a bazillion updates needed doing. When asking why they have not applied the update the answer is usually “oh that’s what that thing is flashing at me for”. In larger companies updates should be scheduled and run from the server (to save on bandwidth mostly, and in some cases to be able to control which updates should be installed), remote devices should be able to be locked and wiped as a bare minimum requirement if they can’t be fully controlled. We have seen instances where this is not happening correctly and have suggested using a tool like Intune.
10. Poor practise
If it is not broken don’t go looking for issues, mentality. What with all of the above to deal with one would assume that an IT technician needs to keep on the lookout for vulnerabilities, but you know what they say about assumptions.
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Bongo IT’s Top 10 Gotchas on Office 365
Of course you don’t want to make a hash of it, and you want a good ROI, but many businesses make a total mess of their migration to Office 365. It should be simple, and if you’ve only got a few users and a small volume of data it can be. But most migrations fail to deliver the promised benefits.
Independent research suggests that 72% of Office 365 migrations of over 200 users fail to deliver significant benefits whereas those “properly” migrated save significant cost and dramatically increase efficiency. With this background, here are 10 confusing pitfalls of Office 365 you should be aware of before migrating to the cloud:
1. Microsoft Account vs O365 Organisation Account
As you will know there are a lot of different versions of Office 365; for home, for Business, for Enterprises, for Not-for-Profit organisations...and even some free versions for consumers requiring a different MS account type not to be confused with your organisational account. If you have both account types (which could even use the same email address) Microsoft will be holding your credentials within two different databases...thing is they sometimes "cross streams", and as we all know you don't want to do that. I'll try to explain the two account types:
Organisational
I have This email address is being protected from spambots. You need JavaScript enabled to view it. as my Office 365 username. This is my organisational account (for Bongo IT) and allows me to access my organisations' apps and data when logged in to the portal. This account is used for logging in to all Office 365 features, for example:
- Office 365 Exchange mailbox
- Office 365 SharePoint
- Skype for Business
Microsoft Account
I also have This email address is being protected from spambots. You need JavaScript enabled to view it. which I have linked as a Microsoft Account (https://signup.live.com). I can use this account type to access the consumer version of OneDrive, and a few other apps. Anyone can have a Microsoft Account like This email address is being protected from spambots. You need JavaScript enabled to view it., or This email address is being protected from spambots. You need JavaScript enabled to view it. and if you want free personal email and storage it’s not a bad idea to get one. In my case as I already had Gmail and didn’t want another email address to remember I just linked that up as my MS account. This account is used for:
- Log in to Windows 8+
- Log in to Skype / Xbox
- Log in to OneDrive (onedrive.live.com)
- Log in to free MS Office (www.office.com)
- Log in to Windows Phone 8+
- My free MS Account apps
With Microsoft things are never simple when it comes to licensing but the key thing is to remember that these account types are stored in separate databases that are not aware of each other. Each allows you access to different things, for example Skype Vs Skype for Business. If using both systems at the same time it is useful to use 2 browsers (one for each) to avoid any logging in issues, and to avoid a great deal of confusion. A password manager won't go amiss either. You may also come a cropper to a few inconsistencies. For example you can link Office 365 Home, or Student, to Skype. You can’t link Office 365 for Business to Skype.
2. Sharing Documents Externally
This used to be quite tricky but Microsoft have worked out some of the bugs since 2013, which has made this a lot more user friendly. There are various ways to share documents/folders/sites with external users but you need to be aware that SharePoint has a different security setup to OneDrive (paid subscription). OneDrive is ready to go when it comes to sharing externally, SharePoint Online (SPO) may require some settings updating and security groups creating. If you decide to allow internal users to be able to share a Site in SharePoint be extremely cautious.
Before you start you will need to turn on External Sharing in your Admin Centre, from the SharePoint dropdown menu item. NB: You can only share documents etc. with a Microsoft Account or Organisational Account holder. These are the things to be aware of: Sharing by email address: if you opt for this and uncheck "Require sign-in" the user will be emailed a Guest link. They could email this on to anyone (with a MS Account) who would then be able to access the data. Make sure you set an expiry date to the link. Sharing by "Get a Link"; again you will see options where no sign in is required. Remember to set an expiry if that is an option you choose.
3. Failing to factor in the Cost of Add-ons
As a Microsoft cloud partner it’s almost easy to forget that we have access to almost everything as part of our partnership benefits. Gloating aside here are some of the Add-ons you might want; Dynamics CRM Online, Yammer for Enterprise, Project Pro for Office 365, Visio Pro for Office 365.
4. Using Exchange Server Deployment Assistant
The Exchange Server Deployment Assistant will help you build a step-by-step checklist that will greatly assist you in the deployment of Exchange Server for different scenarios. It is a web based tool, and can be found here. If you don’t use the tool, then you are risking looking like one.
5. Get the prerequisites right for Office 365 when going hybrid
If you have large files which need super fast access (e.g. architects, designers, engineers), or you have offices in multiple countries you are probably considering going for a hybrid deployment. Number one is to be aware that if you have older software you need to upgrade it to support Exchange 2007 and later. However if you are using 07 and 10 you still need a 2013 CAS&MB server. We would recommend upgrading your entire on premise organisation to 2013. With Exchange 2016 around the corner it makes a lot of sense to get on the upgrade path now before you get left woefully behind, lacking in various bit of new functionality.
6. OneDrive for Business 5000 limit…and why you shouldn’t use it, yet.
Whilst you may have carefully planned your libraries, data migration and access rights you may not know about the 5000 limit which will scupper your good intentions at the final stage. You can only sync 5000 items (files + folders) per library using the OneDrive for Business app for PC and Mac. It's only a limit of the app, not SharePoint Online. So the answer is either to not sync libraries, or to ensure they only have a limited number of items in them. You can cheat by using Zips but that's not desirable for eDiscovery, or generally for access. We will say this though: currently we do not recommend using OneDrive for Business as it can be (but not always) unstable.
There is a new next gen sync client based on the more reliable consumer version out now but it only works with OneDrive (business not consumer), not SharePoint which is what we need. A little bird a Microsoft has said that it will be released in July 2016 though. Currently OneDrive for Business is unreliable, and whilst “easy” to fix it can be a bit of a time waster. There is a way round it though that gives you just about the same functionality. You can view SharePoint Online via the Explorer window so long as you are using Internet Explorer and select that option in the library settings pane. You can eliminate issues with the local cached copies of files by going old school and mapping a drive to a folder or library.
7. Calculating time to upload - EWS 400GB limit, and bandwidth requirements.
An oft forgotten issue when you are bogged down with the technical details. If you have a slow upload rate then you need to think carefully about how you are going to move all your company data to the cloud. You might even consider moving some data to another site to increase the upload speed. Exchange Web Services (EWS) also has a 400Gb transfer limit per day set as well. If you are uploading this much data the chances are you will be doing the migration in stages over multiple days, but it is still something to be aware of.
8. Data Retention: 14 day retention limit for deleted items.
As an Administrator you will be able to reinstate files which the user may have accidentally (or deliberately!) deleted from their Exchange Online inbox or from SharePoint Online. However the default setting is that files will only be retained for 14 days which doesn’t give the business much time to react in the case where something has gone missing.
9. Being aware that Lync Online does not provide full VoIP telephony…yet
If you thought that Office 365 (in the UK) was a full Unified Communications platform you would be wrong. Yes you can host Skype for Business (Lync), or use a hosted service but this requires significant investment. In its virgin state you can't use Skype for Business to dial out, which is a shame. Microsoft look like they will be releasing full PTSN integration at some point in the near future though, this feature is available now on a trial basis depending on your location and account type. We are trialing it right now!
10. Spam filtering – do I hear a rewind!
You may have spent years tuning your spam filter so that you barely get any spam at all but, like unlike Viking Gold, you can't take it with you. You will need to learn about Exchange Online Protection (EOP). There is so much material out there on EOP that there is little I could add so try reading up on it here... more details NB: If you have a Hybrid deployment or just plain old Exchange or even a non-Microsoft email server (heaven forbid) you can still get EOP to protect your mailboxes!
- For both Exchange Online and SharePoint Online you need to be aware of the legal retention framework which your business operates under. Solicitors and accountants will have a completely different set of rules to play by than a builders. The general principal is the same though, retain data only for as long as you legally need to. This reduces your “legal risk”.
- For Exchange Online you can now edit this limit by creating a new MRM policy; here's how MS Blog You may also wish to use the Exchange Admin Centre or PowerShell Technet
- For information on how the SharePoint Online Documentation Deletion Policy Centre works try this very helpful article Technet
Enjoy the blog post? Then you would love our newsletter! Sign up here Signup and get a free Office 365 pitfall PDF guide
Call us on: 01865 988 217
Email continuity during an Office 365 Cutover migration
Ever been in the position where you can’t access your emails? Then you will know that sinking feeling, and the ‘sh1t I can’t do any work’ thoughts that will run through your head.
-
FREE IT STRATEGY SESSION
-
At Bongo IT, we know that technology is increasingly dominant and crucial to maintaining business performance and productivity.
Organisations should make sure they are making the right IT decisions for their current needs, whilst also planning for the future with flexible and scalable solutions.
-
As a special offer, we are offering a FREE one hour consultation to address your current IT setup and recommend an effective strategy for your future requirements.
Addressing issues such as computer hardware, broadband, data security, file sharing, compliance and more, we’ll help you build a plan and ensure you deploy the most cost-effective IT strategy for your company’s needs.



















